Why is testing conducted?
Building effective cybersecurity
Compliance with Russian standards and laws (GOST 57580, Central Bank Regulations, 152-FZ, 187-FZ)
Elimination of consequences and prevention of information security incidents
What is tested
ㅤ
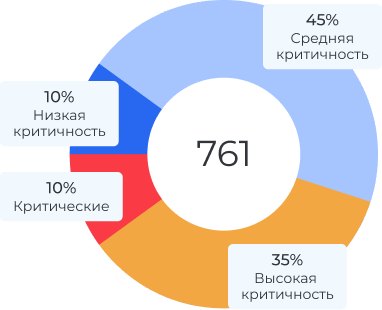
How many vulnerabilities did we find?
The statistics are based on the last 100 projects of various types: external perimeter penetration testing, internal infrastructure penetration testing, web applications, mobile applications, APIs, and specific protocols.
Penetration testing tools
While working on projects, we often create our own tools: we write scripts, exploits, and automate routine tasks for a specific project.
Reconnaissance and information gathering
- BBOT, ReconFTW, Amass
- Gitleaks
- Wappalyzer
- Shodan, Censys
Detailed review and manual analysis
- Burp Suite, Postman, cURL
- Metasploit
- Linux console utilities
- Python/Bash/JavaScript
Universal vulnerability scanners
- Nmap
- Burp Suite
- Nuclei
We use all testing methods.
The testing methodology is agreed upon with each customer individually. However, it is always based on industry best practices, standards, and guidelines, such as NIST SP800-115, WSTG (Web Security Testing Guide), OSSTMM (Open Source Security Testing Methodology Manual), and others.




What is included in the test report
For each type of testing, a detailed report is created, which describes in detail:
All vulnerabilities found
Possible attack vectors, supported by screenshots
Recommendations for eliminating vulnerabilities
The report structure includes three sections that will be useful for:
Information security professionals
Customer company management
IT specialists
Stages
-
Preliminary stage and passive reconnaissance
Gathering information from open sources
-
Scanning and active reconnaissance
Thorough scanning of customer resources using automated tools
-
Detailed analysis of resources and manual analysis
This stage reveals the largest number of vulnerabilities. Manual testing expands the scope of work and identifies logical vulnerabilities that are difficult to detect with automated tools
-
Exploitation
Findings from all previous testing stages are used to simulate attacks by real attackers and gain unauthorized access to resources.
-
Documentation and reporting
From 450,000 ₽
From 20–25 business days
Pricing is determined individually based on your scope, IT infrastructure, and tasks. The cost of services depends on the complexity and volume of work, and we are always ready to offer you the most favorable terms based on the price/quality ratio.
Advantages of working with us
We are always in touch and respond quickly to all questions
Our clients
FAQ
Penetration testing is performed by information security specialists who are proficient in professional tools and techniques.
There are two main types of testing:
- External penetration testing simulates the actions of an external attacker attempting to penetrate the system via the Internet.
- Internal penetration testing assesses the risks posed by insiders who have access to the infrastructure.
The result of the work is a report listing the vulnerabilities found, ways to exploit them, and recommendations for elimination. The document also includes a description of the tests performed and the methods used.
Important: penetration testing is only carried out with the permission of the system owner and in strict compliance with the law.
Features of CPT:
- Continuous testing instead of periodic checks.
- Use of automated tools for monitoring and analysis.
- Quick response to updates and changes in systems.
- Black Box: testing without access to internal information. An attack from outside is simulated.
- Grey Box: specialists have limited data (for example, an account without privileges). Allows you to focus on critical points.
- White Box: full access to architecture, code, and internal systems. Used for comprehensive testing and analysis of operating logic.
- At least once a year;
- When updating or scaling infrastructure;
- When launching a new IT landscape or changing the security perimeter.
- Compliance with standards and regulatory requirements (PCI DSS, GOST R 57580, 719-P CB RF, etc.);
- Prevention of incidents;
- Verifying the effectiveness of existing security measures;
- Identifying and eliminating vulnerabilities;
- Assessment of security management processes;
- Justification of investments in information security;
- Preparation for possible attacks.
- Banks and financial institutions — in accordance with the Regulations of the Bank of Russia.
- Critical information infrastructure (CII) entities — in accordance with FSTEC Order No. 239.
- Any companies interested in an objective assessment of their level of security and prevention of reputational and financial losses.