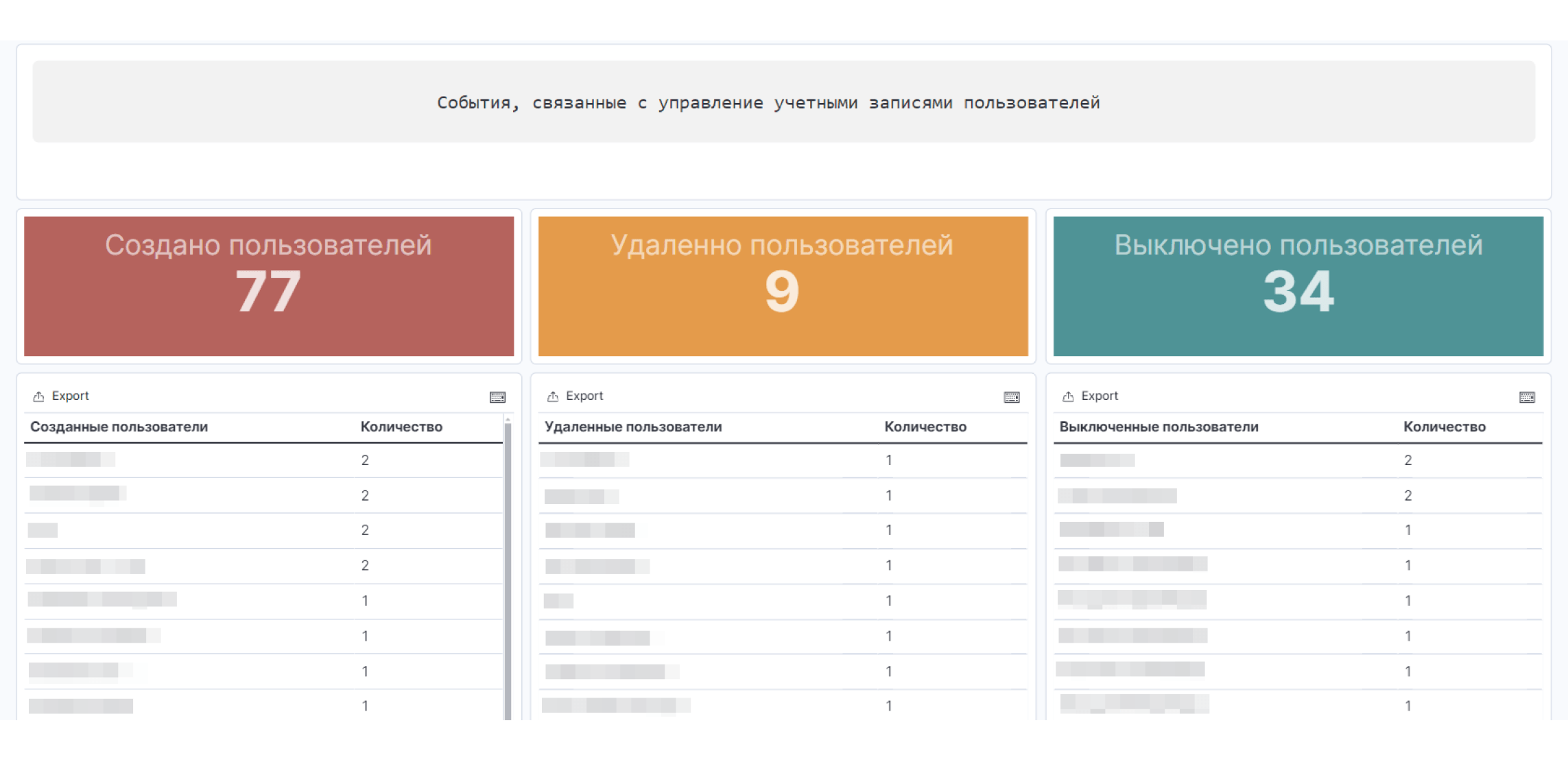
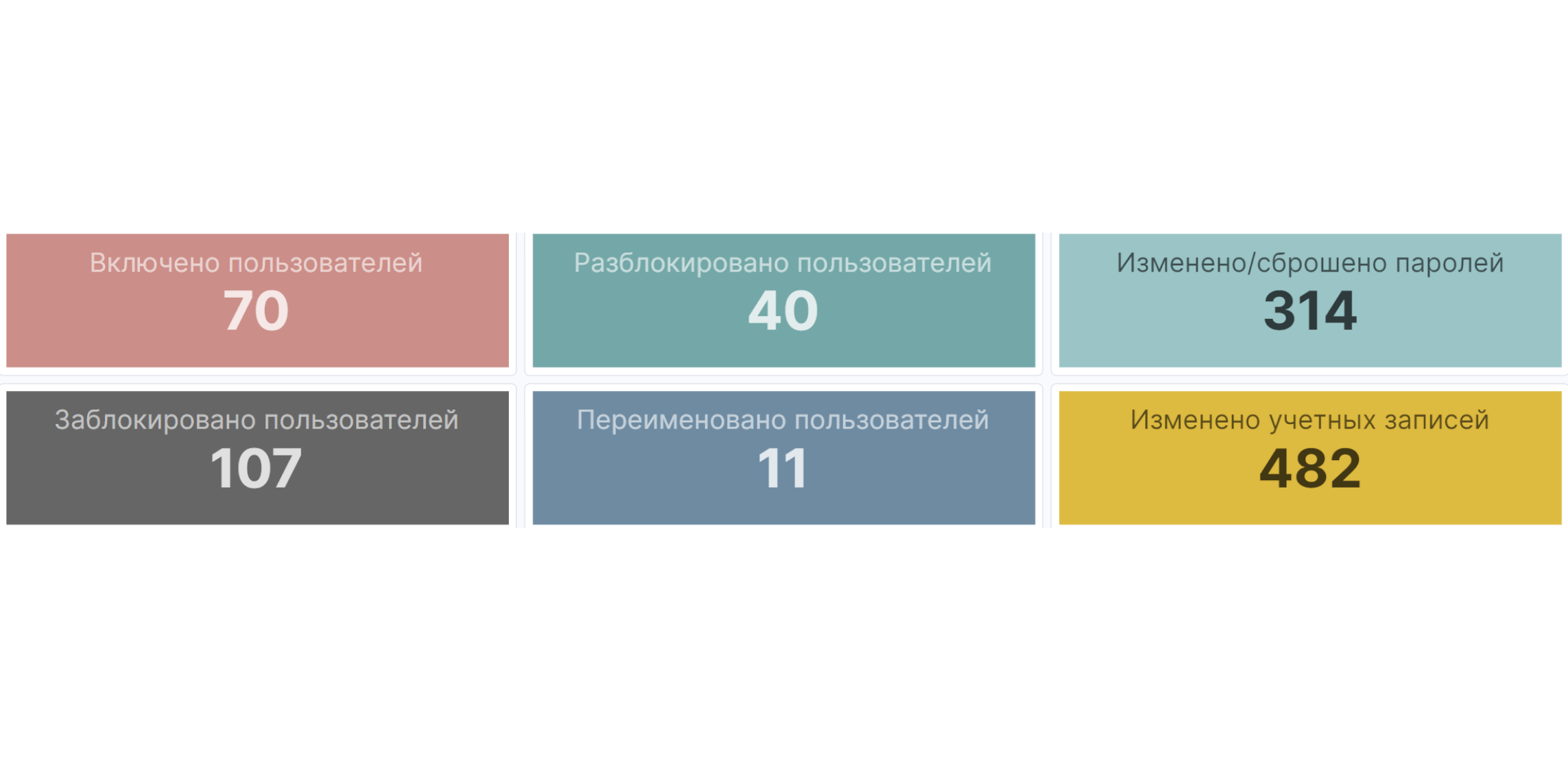
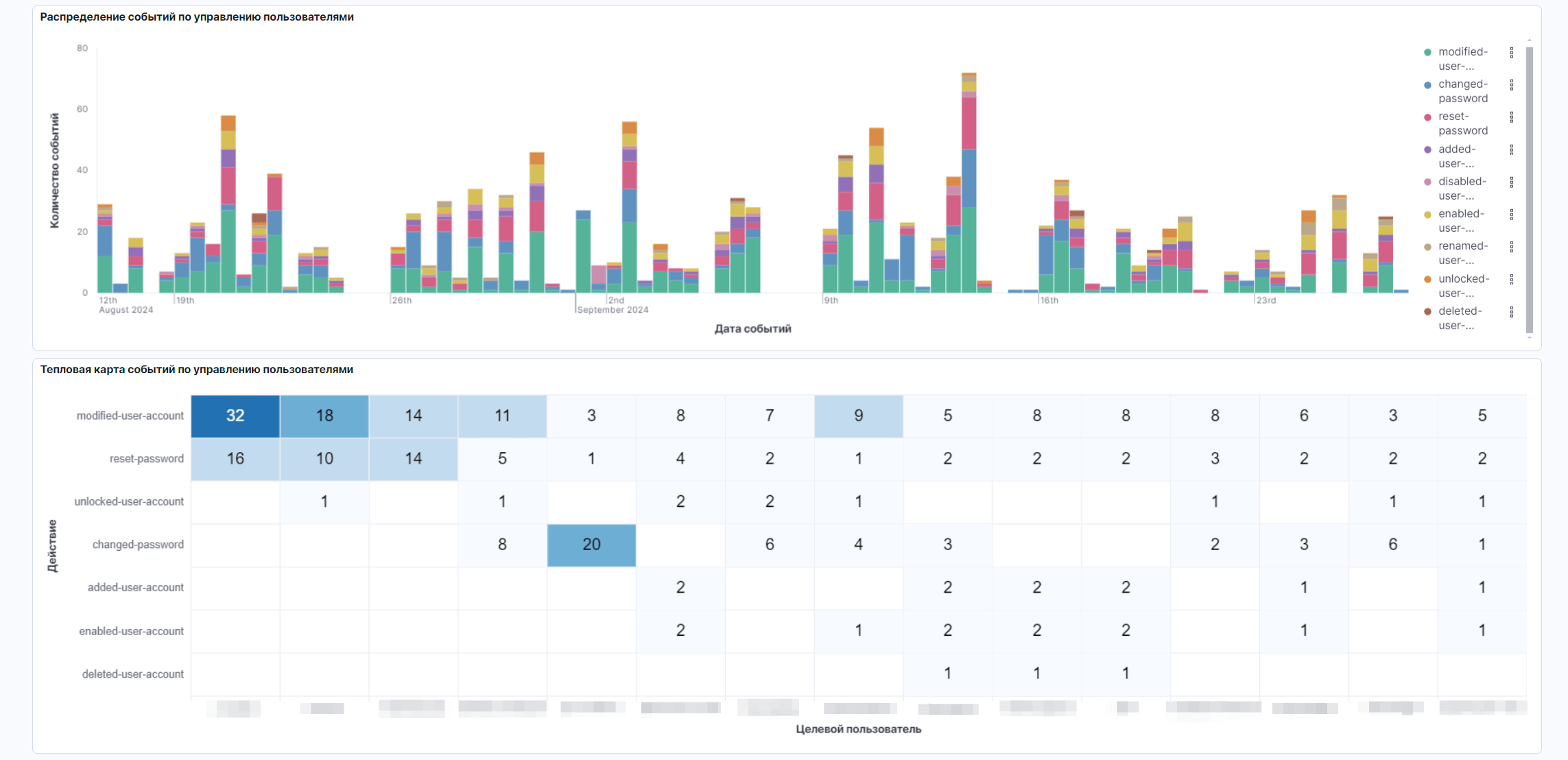
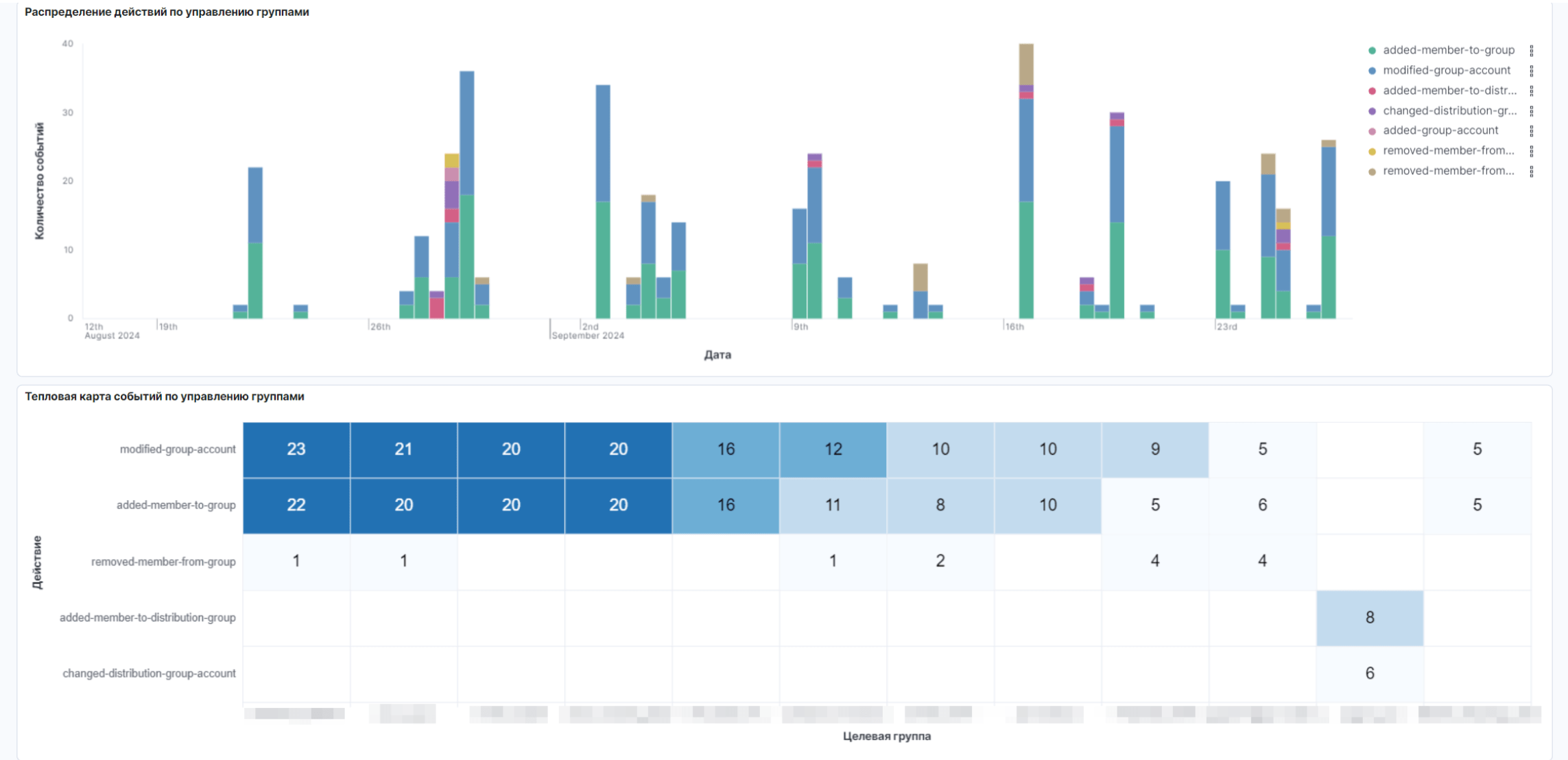
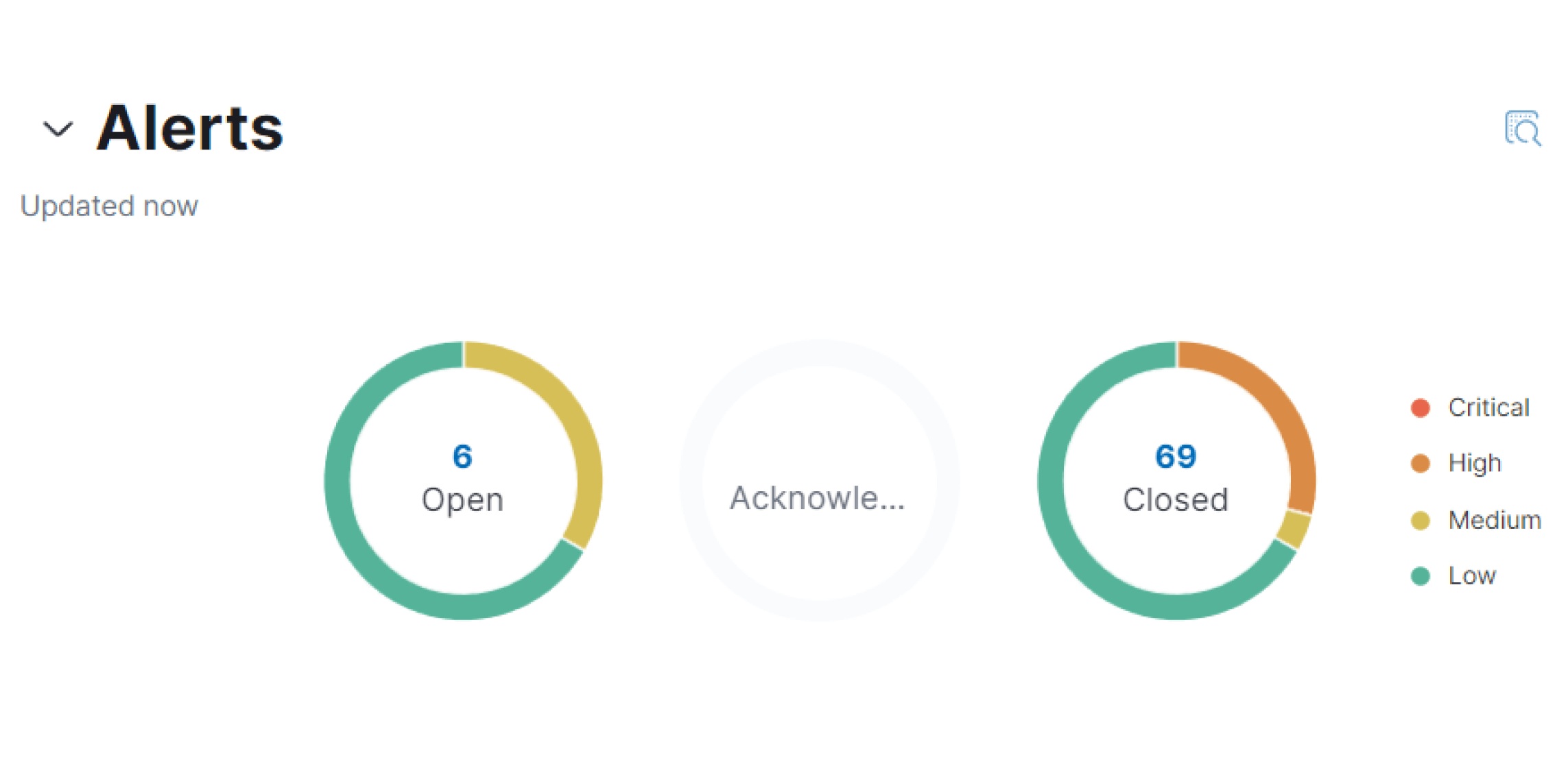
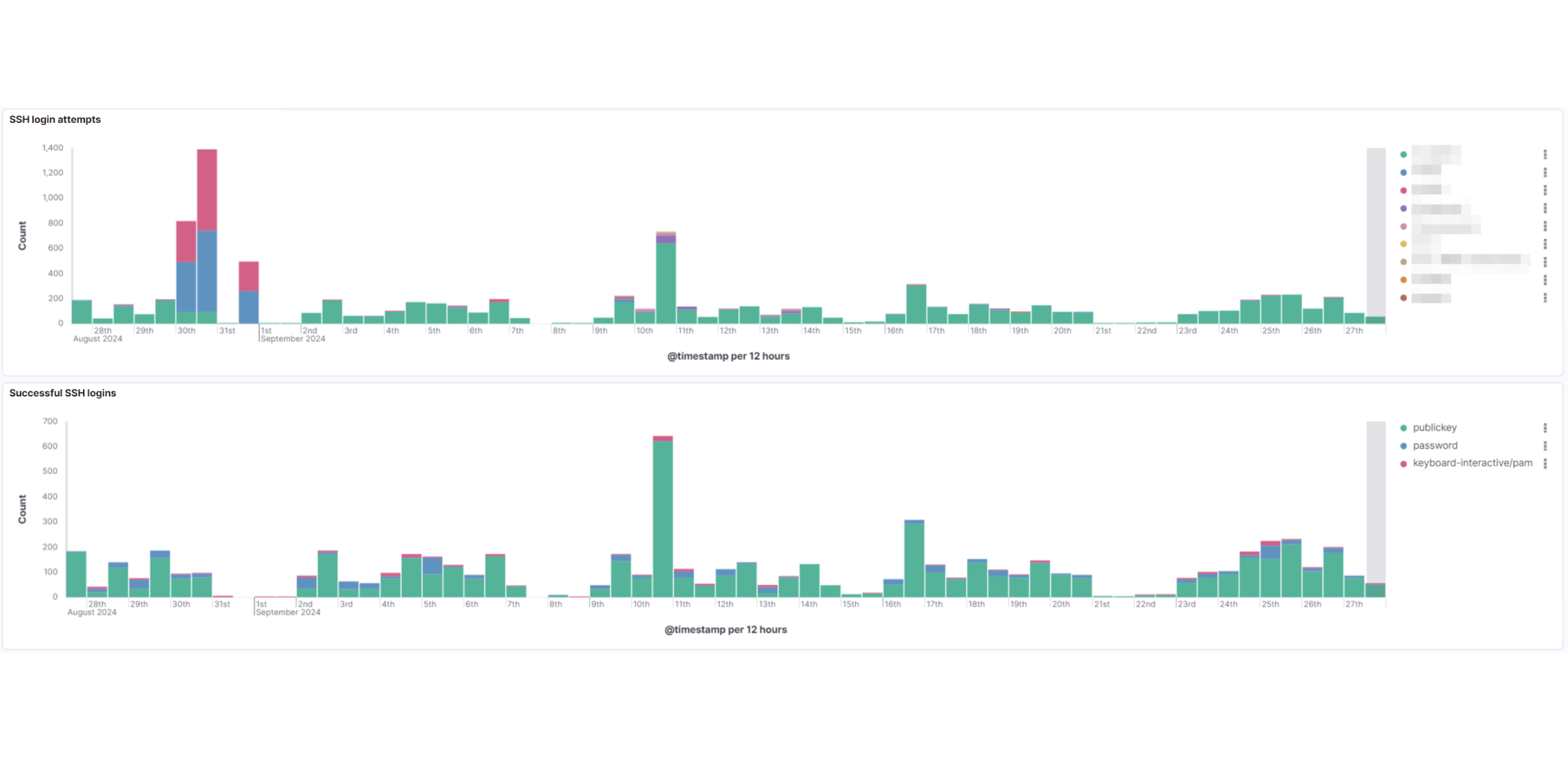
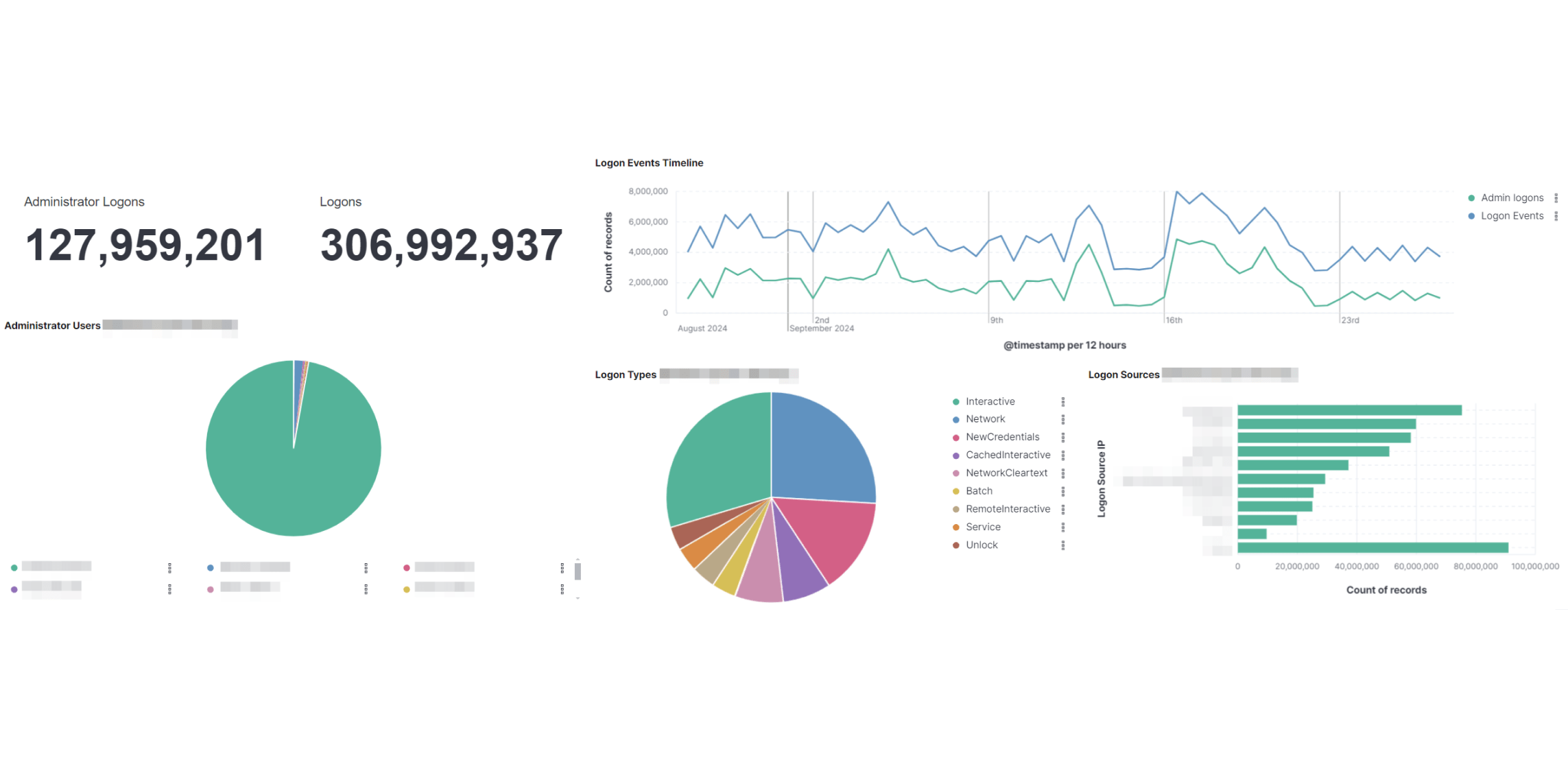
Что такое Security Operations Center
Security Operation Center (SOC) — сервис, который помогает защищать ИТ-инфраструктуру компании, обнаруживая атаки раньше, чем злоумышленники успевают нанести вред. Основная задача — мониторинг и предотвращение киберугроз в реальном времени.
Зачем это бизнесу
Предотвращение кибератак
Снижает вероятность успешных атак и уменьшает связанные риски
Поддержание непрерывности работы
Обеспечивает стабильность функционирования систем и предотвращает простои
Соответствие требованиям
Помогает выполнять законодательные и отраслевые стандарты по защите данных
Что входит в услугу
- Сбор журналов событий на компонентах инфраструктуры
- Детектирующая логика обнаружения атак
- Время реагирования на инциденты
- Порядок уведомления об инцидентах и подозрительных действиях
- Качество сведений для реагирования на инциденты
- Клиентский кабинет SOC
Как SOC обрабатывает подозрительные события
| Приоритет | Время оповещения | Способ оповещения |
| Критический | Не более 30 минут после выявления подозрительного события | 1. Личный кабинет
2. Сообщение в Telegram-чат 3. Звонки на телефоны / электронная почта и др. |
| Высокий | Не более 40 минут после выявления подозрительного события | |
| Средний | Не более 60 минут после выявления подозрительного события | |
| Низкий | Не более 90 минут после выявления подозрительного события |
Типовые анализируемые события
2 x 48 core
Запуск/остановка служб
и процессов в ОС
Изменение привилегий
для учетной записи
Попытки сброса/
изменения пароля
Неуспешный вход учетной записи в систему
в рабочее/не рабочее время
Изменение политик регистрации
событий безопасности
Изменение параметров технических средств
защиты информации
Множественные неуспешные попытки аутентификации
Очистка/удаление журналов регистрации событий
Отключение/изменения уровня логирования
Выход из системы
Изменение привилегий для учетной записи
Запуск несанкционированых скриптов
Типовые источники событий
- Система антивирусной защиты от вредоносного ПО
- Системы защиты от несанкционированного доступа
- IPS/IDS (Система обнаружения/предотвращения вторжений)
- NGFW Next-Generation Firewall
- WAF (web application firewall)
- Другие CPB
- Электронная почта
- Централизованное управления виртуальной инфраструктурой
- Система управления базами данных (СУБД)
- Веб сервер
- Система резервного копирования и архивирования
- CRM (customer relationship management)
- IDM (identity and Access Management) / PAM (privileged access management)
- ERP (Enterprise Resource Planning)
Этапы внедрения и эксплуатации
-
Установка сетевой связанности между инфраструктурой Клиента и сервисом SOC
Для подключения необходим сетевой инженер Клиента. Подключение производится совместно с командой сервиса SOC. От 1 до 3 рабочих дней
-
Предоставление дистрибутива агентов SOC
Со стороны клиента не требуются специалисты.
В течение суток
-
Установка агентов на компоненты ИТ-инфраструктуры Клиента
Для установки агентов со стороны Клиента необходим системный администратор отвечающий за установку ПО на серверах, и рабочих станциях. От 1 до 3 рабочих дней
-
Установка лог-коллектора
Для установки агентов со стороны Клиента необходим системный администратор отвечающий за установку новых компонентов ИТ-инфраструктуры. В зависимости от типа компонента возможно безагентное подключение к сервису SOC. При таком способе подключения в ИТ-инфраструктуру клиента устанавливается ВМ. Образ виртуальной машины лог-коллектора предоставляется специалистами сервиса SOC. От 1 до 3 рабочих дней
-
Настройка передачи событий безопасности с сетевого оборудования Клиента
Для настройки передачи событий безопасности с сетевого оборудования со стороны Клиента потребуется сетевой инженер или системный администратор. От 1 до 2 рабочих дней
-
Настройка расширенного логирования на всех компонентах ИТ-инфраструктуры Клиента
Со стороны Клиента потребуется системный и сетевой инженеры. Инструкции по настройке предоставляют специалисты сервиса SOC. от 1 до 3 рабочих дней
-
Передача, анализ, хранение и непрерывный мониторинг событий безопасности в режиме 24/7
После успешного внедрения, сервис переходит в режим постоянного мониторинга, в рамках которого специалисты на разных уровнях поддержки анализируют все подозрительные события ИБ. Реакция Клиента требуется только в случае подтверждения подозрительных событий или инцидентов ИБ.
Услуга позволяет выполнить требования
- ГОСТ Р 57580.1-2017: меры МАС.1-МАС.8, МАС.10-МАС.23 (возможный прирост к оценке по ГОСТ — 0,06);
- Приказ ФСТЭК России №21 и №17: требования РСБ.1-РСБ.7, РСБ.8 (17-й приказ);
- ФЗ-187: Статья 4. Принципы обеспечения безопасности критической информационной инфраструктуры, включая требования по ГосСОПКА;
- PCI DSS: требования 10.1 (включая подпункты), 10.2 (включая подпункты), 10.3 (включая подпункты), 10.5 (включая подпункты), 10.6 (включая подпункты), 10.7 (включая подпункты), 10.8.;
- Приказ ФСТЭК России №239: АУД.4-АУД.9.
Команда сервиса SOC
Менеджеры сервиса
Инженеры сервиса
Системные инженеры сервиса
Специалисты по работе с SIEM системой
Аналитики 1-го уровня поддержки
Аналитики 2-го уровня поддержки
Используемые технологии
Личный кабинет сервиса
Централизованная обработка событий ИБ
Компоненты EDR
Предотвращение вредоносной активности на конечных точках: подключенных к сети рабочих станциях, серверах, устройствах Интернета вещей и т.д.
Компоненты Threat Intelligence
База знаний об угрозах, полученных в результате анализа и интерпретации данных
Преимущества от ITGLOBAL.COM Security
Время реакции команды SOC – не более 10 минут в любое время дня и ночи
Условия обслуживания известны заранее и не нарушаются
Предоставление доступа к SIEM-системе для просмотра “сырых” логов и дашбордов
Разработка нестандартных правил корреляции по запросу Клиента
В конце каждого месяца мы предоставляем отчет, в котором:
- Общий перечень событий, зарегистрированных за отчетный период
- Перечень подозрительных событий ИБ, не являющихся инцидентами
- Описание инцидентов ИБ, выявленных за отчетный период
Дополнительно отчет может содержать и другую информацию, относящуюся к результатам оказания Услуги за период.